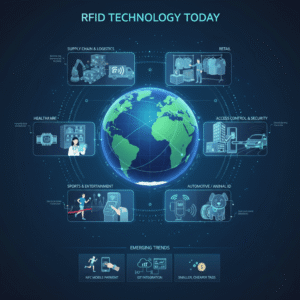
Choosing the wrong tag memory location creates future problems. This can lead to system failures or security breaches. Learn the different memory banks to ensure your project's success.
To choose the correct programming location, match your data needs to the specific memory bank. Use EPC for dynamic IDs1, User memory2 for flexible data, and TID for a unique, unchangeable identifier. Secure data using the Reserved memory3 for passwords.
That's the short answer. But as a buyer, you know the details matter. Each memory bank has a specific job. In my 20 years at Fongwah, I've seen projects succeed or fail based on this one choice. I started on the production line, so I understand these tags from the inside out. Let's break down each option. This will help you make an informed decision for your own system.
Which Gen 2 memory bank should you use for your data?
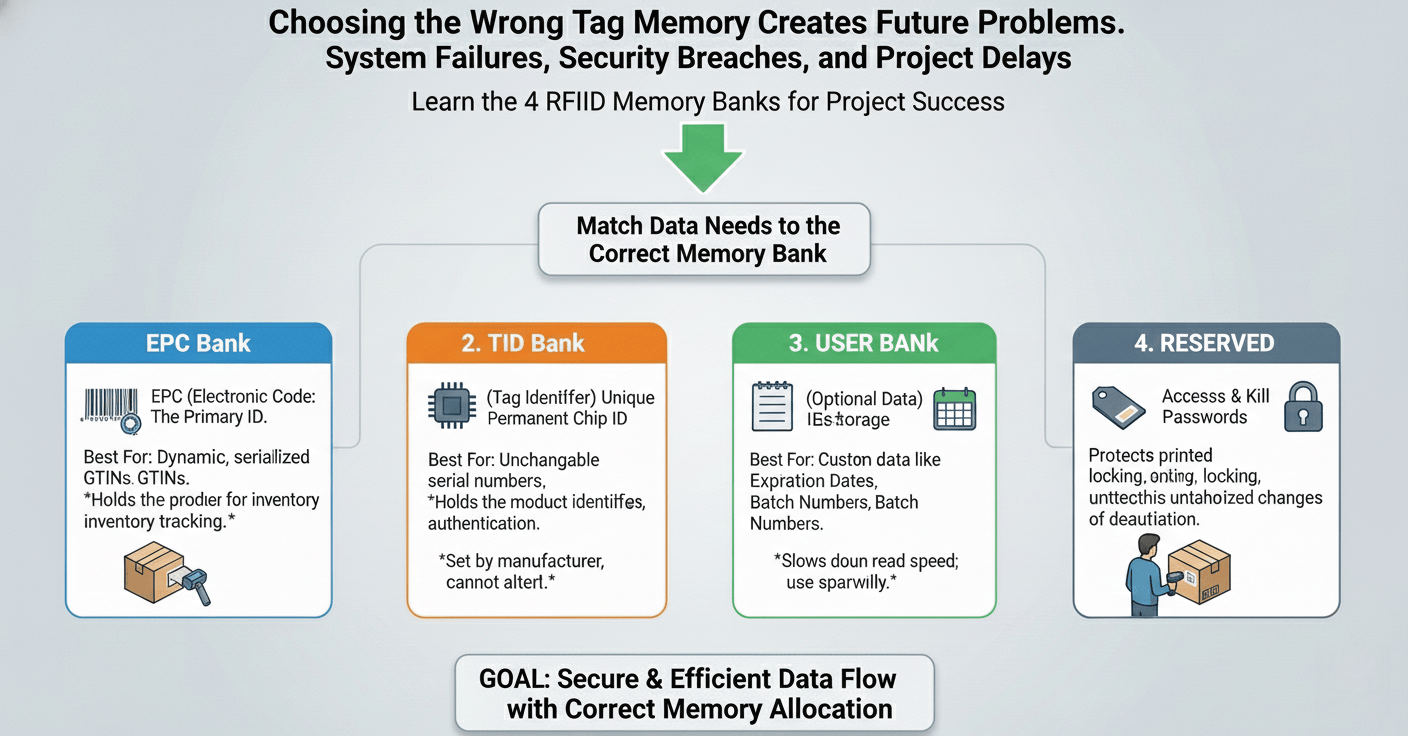
Storing data in the wrong bank causes confusion. This can make your entire RFID system inefficient. Let's look at the specific purpose of each memory bank for clarity.
Use the TID bank for the tag's unique, factory-set serial number. Program your item's unique identifier in the EPC bank. Store additional, flexible information in the User bank. The Reserved bank holds kill and access passwords for security.
Choosing the right memory bank is fundamental. I remember a client in logistics who was storing shipping manifest data in the EPC bank. Their read speeds were slow because the EPC bank is optimized for quick, unique identification, not large data blocks. They had to reprogram thousands of tags. From a buyer's perspective, this kind of rework is a costly disaster. You need to align the data's function with the memory bank's intended design.
Unique Identification (TID & EPC)
The TID and EPC banks are both for identification. But they serve very different roles. The TID is permanent. Think of it like a hardware serial number that never changes. It guarantees the tag itself is unique. The EPC is what you program. It identifies the item the tag is attached to. It is designed to be read quickly and must be unique within your system.
Flexible Data and Security (User & Reserved)
The User memory2 is your flexible storage4 space. It’s perfect for data that might change, like maintenance logs, shipping dates, or product temperatures. The Reserved bank is purely for security. It stores the Access and Kill passwords. The Access password controls who can write to the tag. The Kill password permanently deactivates the tag.
| Bank Name | Primary Purpose | Writable? | Common Use Case |
|---|---|---|---|
| TID | Unique Tag Serial Number | No (Factory-Set) | Anti-counterfeiting, Tag verification |
| EPC | Unique Item Identifier | Yes | Product tracking, Inventory management |
| User | Additional, Flexible Data | Yes | Maintenance records, Sensor data |
| Reserved | Security Passwords | Yes | Access control, Tag deactivation |
Unsecured tag data is a huge risk. Anyone could clone or alter your information, causing major disruptions. You can protect your data with passwords and memory bank locking.
Protect data by setting an Access Password5 in the Reserved memory3 bank. This password is required to write to the EPC6 or User memory2. You can also permanently lock memory banks to prevent any future changes, making them read-only.
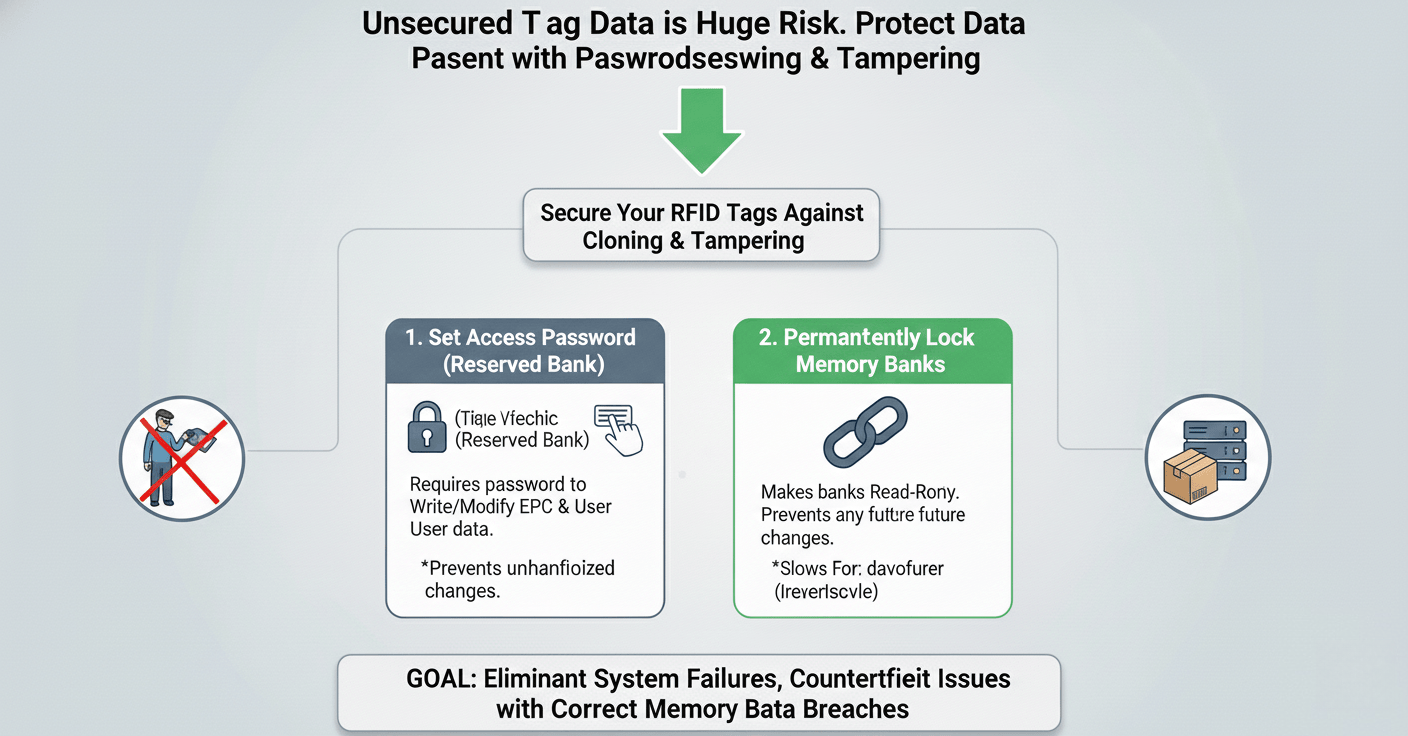
As a buyer, data integrity7 is not just a technical spec, it's a core business requirement. We had a customer who tracks high-value medical equipment. Someone could theoretically rewrite a tag to hide an asset or change its maintenance status. This would have serious consequences. We helped them implement a password strategy. Now, only authorized personnel with the correct password can update a tag's service history. This simple step secured their entire asset management process. Security features are not add-ons; they are essential for a robust system.
Using Passwords for Controlled Access
The Access Password5 is your first line of defense. It is a 32-bit value stored in the Reserved memory3 bank. When a password is set, a reader must provide it before it can write new data to the EPC, User, or even the password area itself. This prevents unauthorized changes but still allows for updates by trusted users. It offers a great balance between security and flexibility.
Permanent Locking for Finality
For maximum security, you can permanently lock a memory bank. This is a one-way action. Once a bank is locked, it becomes read-only forever. This is useful for data that should never change, like a product's initial commission date or a unique serial number you've encoded in the EPC. But be very careful. A mistake here cannot be undone.
| Security Method | How it Works | When to Use | Reversible? |
|---|---|---|---|
| Access Password5 | A 32-bit password is required to write data. | For data that needs to be updated by authorized users. | Yes, if you have the old password. |
| Permanent Lock | A command makes a memory bank read-only forever. | For critical data that must never be altered after programming. | No, it is permanent. |
Can you change RFID tag data after it has been programmed?
You might think programming a tag is permanent. This fear can stop a project, worrying about future needs. But most memory banks are designed to be changed.
Yes, you can change data in the EPC and User memory2 banks many times, unless they are locked. The TID is factory-programmed and cannot be changed. The Reserved memory3 for passwords is also rewritable.
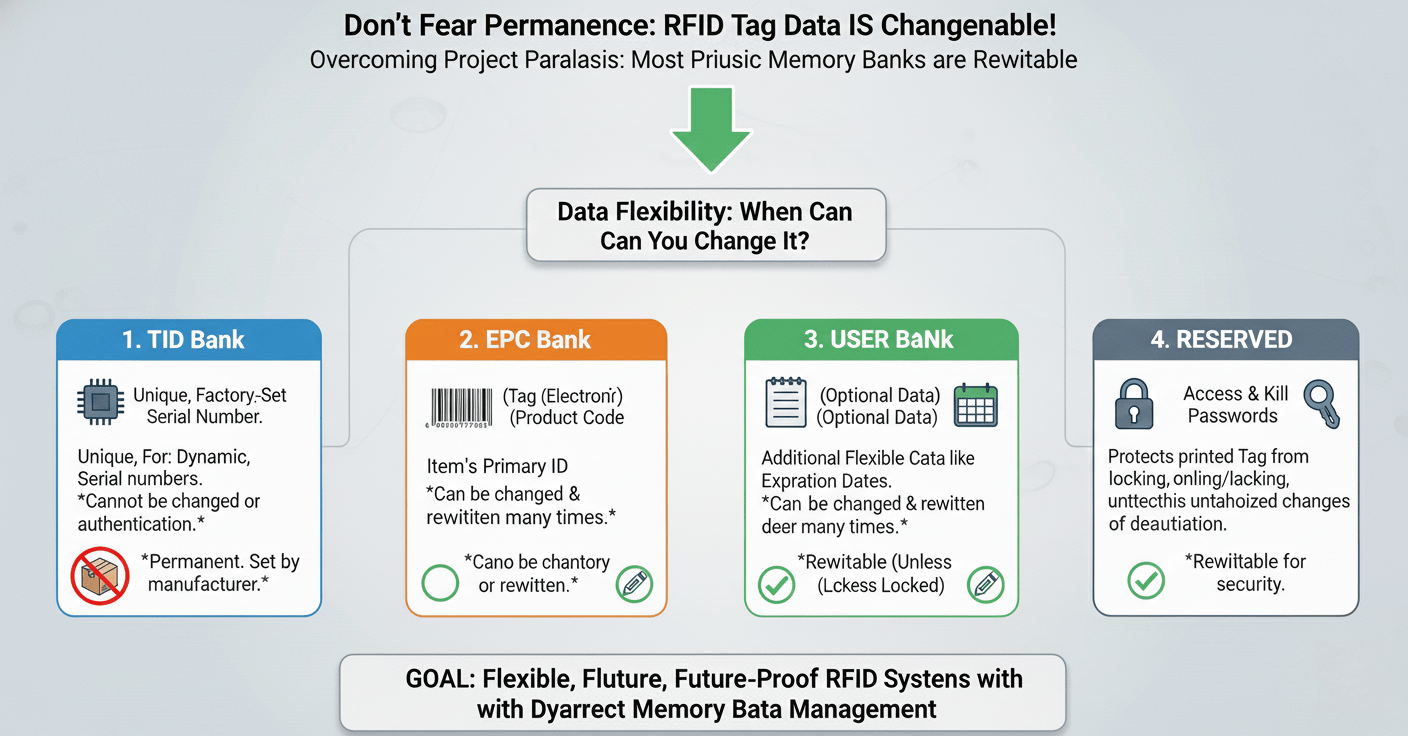
Flexibility is a major factor when you are buying thousands of tags. Imagine you are a retailer. I worked with a client who tagged all their seasonal apparel. After the season, they wanted to move unsold items to an outlet store. Because they used the User bank for pricing and the EPC for the SKU, they could easily rewrite the tags for the new store. They did not have to buy new tags. This saved them a lot of money. The ability to rewrite tag data directly impacts your long-term return on investment8 (ROI). It turns a single-use tag into a multi-purpose asset.
The Flexibility of EPC and User Memory
The EPC and User memory banks are designed for multiple read/write cycles. Most modern UHF Gen 2 tags can be rewritten at least 100,000 times. This allows you to adapt as your business processes change. You can update an item's status, location, or associated data throughout its lifecycle. This makes your RFID system dynamic and responsive to real-world operations.
The Permanence of the TID
The one exception is the TID bank. It is written once at the factory when the chip is made. You cannot change it. This is a feature, not a limitation. It provides a stable, unalterable identifier for the physical tag itself. You can always count on the TID to be the same, which is crucial for applications where you need to verify that the tag has not been swapped or tampered with.
| Memory Bank | Changeable? | Typical Rewrite Cycles | Strategic Use |
|---|---|---|---|
| TID | No | 0 | Proving tag authenticity. |
| EPC | Yes (if not locked) | 100,000+ | Updating item status or location. |
| User | Yes (if not locked) | 100,000+ | Changing associated data over time. |
| Reserved | Yes (if not locked) | 100,000+ | Updating security credentials. |
Conclusion
Choosing the right memory bank is key. Match the bank to your data's purpose, security needs, and future flexibility. This ensures a successful and reliable RFID system.
---Understanding dynamic IDs can improve your data management strategies in RFID applications. ↩
Exploring User memory can help you leverage flexible data storage in your RFID systems. ↩
Understanding Reserved memory is crucial for implementing security measures in RFID systems. ↩
Exploring flexible storage options can improve your RFID system's adaptability. ↩
Exploring Access Password functionality can enhance your RFID security protocols. ↩
Learning about the EPC bank can optimize your item identification processes. ↩
Understanding data integrity measures is essential for maintaining reliable RFID operations. ↩
Exploring ROI in RFID can guide your investment decisions for better financial outcomes. ↩